TLDR. Keycloak is an open-source Java-based Identity and Access Management (IAM) tool developed by the RedHat community under Apache License 2.0. Being an Identity and Access Management (IAM) tool, it streamlines the authentication process for applications and IT services.
In an internet era seasoned with GDPR and privacy regulations, security is a topic that’s receiving more and more attention. As such, plenty of companies invest heavily in ensuring that their software applications are properly secured and that the users of such applications have controlled access to data. Attempting to protect against data spillage that may result in multi-million dollar penalties, companies need to make sure that the users of their software applications are identifiable and have the right authority to interact with certain data..
This is where an IAM comes in, as a centralized system for managing the access rights and identities of the end users, ensuring that the right people in a company have appropriate access to resources. An IAM usually enables functionalities such as Single Sign-On (SSO), identity federation, and strong authentication for the users of the software application.
Why is Keycloack relevant
In one way or the other, most modern applications make use of IAM solutions for managing the identity and access of their users. As such, the developers of such software solutions would need to implement custom user management software for each application that they would be working on. This means that functionalities like login pages, session management, password reset or even social authentication would have to be customly implemented for each software application that the developers would be working on. And all this functionality would have to be maintained and bug free. What a hassle!
Thanks to frameworks like Keycloak, you get everything you need to manage user identities and protect internet resources out of the box. Using the admin console, companies can easily configure system level abilities such as social media authentication, SSO or Active Directory integration. And it all just works, with no changes to the code base!
From an administrative perspective, administrators can streamline and manage all aspects of the Keycloak server, from a special management console, that makes everything extremely versatile.
From an end user perspective, authentication between multiple applications becomes seamless. You use a single authentication form, and have access to all the applications that are part of the specific company, without having to login to each separate application with separate credentials.
Before we can use Keyclock to its full potential, it’s important for us to grasp some internal concepts.
Domain Terminology
1. Realm
You can think of the realm as a tenant. So the first thing you will want to do is create a realm for your application and users. A realm is fully isolated (in terms of configuration, users, roles, etc.) from other realms. Because of this, you can create one realm for internal applications and your employees and another realm for external applications and customers.
2. Client
Clients are entities that can request Keycloak to authenticate a user. Most often, clients are web, mobile and native applications that want to use Keycloak to secure themselves and provide a single sign-on solution. Clients can also use any type of services such as REST APIs, gRPC, or WebSocket that just want to request identity information or an access token so that they can securely invoke other services on the network that are secured by Keycloak.
3. Client Scope
Allows creating reusable groups of claims that are added to tokens issued to a client. You can also define an optional client scope. In this way, you should specify the optional claim with the scope parameter.
4. Roles
Usually represent a role a user has in either your organization or in the context of your application. For example, users can be granted an administrator role therefore they can access and perform any action on any resource in your application. Or, they can be granted a human resources manager role therefore they can only access and perform some actions on limited resources. Keycloak also provides the concept of composite roles. But not using this feature carefully, you can increase complexity so your system will become hard to manage and maintain.
Relevant Features
Understanding the basic domain terminology, allows us to better make use of the exhaustive feature set that Keycloak provides us with. Some features that are relevant in this context are:
Multiple Protocols Support
As for now Keycloak supports three different protocols, namely – OpenID Connect, OAuth 2.0 and SAML 2.0.
SSO
It is a part of the Identity Federation. Users can authenticate by usingKeycloak rather than using their own applications. This means that our applications don’t have to deal with login forms, authenticating users, and storing users. Once we logged in to Keycloak, we didn’t have to log in again to access a different application. This also applied to logout. Keycloak supports single-sign out, which means users only have to log out from the application, it will automatically log out form the authorized application.
Admin Console
Admin console helps to manage all the operations and configurations by the administrators, they can centrally manage all aspects of the Keycloak server. Here we can enable and disable various features, configure identity brokering and user federation, create and manage applications and services, define fine-grained authorization policies, and also manage users, including permissions and sessions.
User Identity and Accesses
Keycloak can be used as a standalone user identity and access manager by allowing us to create a users database with custom roles and groups. This information can be further used to authenticate users within our application and secure parts of it based on predefined roles.
External Identity Source Sync
In case when your client currently has some type of user database, Keycloak allows us to synchronize with such a database. By default, it supports LDAP and Active Directory but you can create custom extensions for any user database using Keycloak User storage API. Keep in mind that such a solution may not have all data necessary for Keycloak to be fully functional, so remember to check if your desired functionality works.
Identity Brokering and Social Login
Keycloak can authenticate users with existing OpenID connect or SAML identity providers. In addition to that, it supports social logins as well such as google, linked-in, Facebook etc. Only we need to select the social network you want to add. We don’t need any code changes to our application. We need only to configure the Identity Provider through the admin console.
Pages Customization
Keycloak lets you customize all pages displayed by it to your users. Those pages are in .ftl format so you can use classic HTML markups and CSS styles to make the page fit your application style and your company brand. You can even put custom JS scripts as part of page customization so possibilities are limitless.
User Federation
User federation is something that uses a single identity across the system. Simply says that we are using Facebook or Google login for most of the application. Keycloak is providing built-in support to connect to existing LDAP or Active Directory servers. We can also implement our own provider if we have users in other stores, such as a relational database or NoSQL Databases.
Workflows
When making use of Keycloack’s features, the following workflows become apparent.
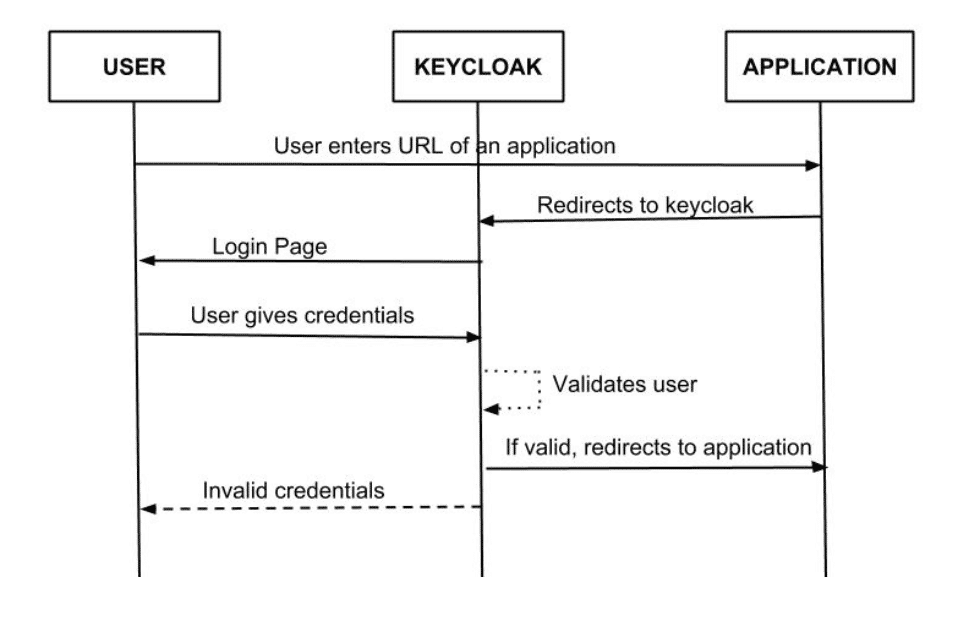
Keycloak workflow
On a complete system secured with keycloak:
A user clicks from a public page to navigate to a protected area within the application. The link to this protected area is in the application settings in keycloak admin console.
- The user will be redirected indeed to the keycloak authentication page. After providing username and password, keycloak redirects the user back to the application again with a code that is valid for a very short span of time.
- The application communicates this code to keycloak along with the application ID and the application secret, then keycloak replies with the Access token, ID token, and a Refresh token. Your application will need only one of these tokens to see which claims the user has, and according to the claims, the user will be granted or denied access to the requested protected URL(s).
Keycloak workflow with OpenID Connect
OIDC is an authentication protocol that is an extension of OAuth 2.0. OAuth 3.0 is only a framework for building authorisation protocols, but OIDC is a full-fledged authentication and authorisation protocol. OIDC authentication flow when integrated with keycloak:
- Browser visits application. The application notices the user is not logged in, so it redirects the browser to keycloak to be authenticated. The application passes along a call-back URL(a redirect URL) as a query parameter in this browser redirect that keycloak will use when it finishes authentication.
- Keycloak authenticates the user and creates a one-time, very short lived, temporary code. Keycloak redirects back to the application using the call-back URL provided earlier and additionally adds the temporary code as a query parameter in the call-back URL.
- The application extracts the temporary code and makes a background out of band REST invocation to keycloak to exchange the code for an identity, access and refresh token. Once this temporary code has been used to obtain the tokens, it can never be used again. This prevents potential replay attacks.

Pros
Here are some of the fundamental advantages that open-source software offers:
- Agility
The development or customization of proprietary solutions depends on the availability and ability of the vendor’s development team to solve the problem. Since open-source solutions are developed by contributions from various community members, they typically offer multiple ways to solve a problem. Hence, you can get the job done faster using an open-sourcing project.
- Cost
As community members develop and maintain open-source solutions, they generally cost less than a proprietary solution.
- Scalability
You can start small by updating the community versions of the open-source project to meet your business requirements. But later, as your business requirements grow, you can leverage commercially supported solutions too.
- Community Engagement
Open-source projects allow developers to create projects and get a platform to interact with other developers outside their organizations.
Cons
An open-source project approach can be a great way to collaborate with other talented engineers. But when you’re building something critical to your business, you need more than a supporting cast of thousands of developers from across the globe. Here are some of the risks observed with open-source software:
- Vulnerabilities Exposure
The source code is available for everyone, cybercriminals can also easily find vulnerabilities in the code. For example, they can extract sensitive information or damage the systems leveraging the open-source software.Here are a few examples of the vulnerabilities found in some common open-source software recently:
-
-
- Severe security flaws were found in the open-source identity and access management solution, Keycloak, which cybercriminals can exploit to gain access to sensitive information in systems leveraging the platform.
- Certain XSS and CSRF vulnerabilities were found in Joomla, an open-source content management solution that cybercriminals can exploit.
- Prior to Cachet version 2.5.1, authenticated users, regardless of their privileges (User or Admin), can trick Cachet and install the instance again, leading to arbitrary code execution on the server.
- An issue was discovered in **Xen **through 4.12.x allowing x86 PV guest OS users to cause a denial of service via a VCPUOP_initialise hypercall.
-
- Security
Open-source project contributors are generally developers who are not security experts. They contribute to the product primarily to support the functionality and may not consider the security aspects. Hence, the open-source product may pose security risks that cybercriminals can easily exploit.
- Warranty
Open-source software does not provide any warranty for its security and support as these products are developed and managed by volunteers.
The developer community members typically test the software for security issues and provide suggestions/recommendations on the public forums, but they are not liable for faulty guidance.
- Security Audit Process
Open-source project contributions are generally managed by a small team to reduce cost. They may not perform proper testing/QA or have a security auditing process at all due to a lack of expertise or workforce.
The testing team may not be familiar with the open-source change requests or test the code properly by considering crucial aspects.
- Copyright
Anonymous developers sometimes develop open-source software. Therefore, it is pretty likely that they may copy from third-party sources without understanding the copyright issues.
As a result, companies leveraging the particular open-source software can be held responsible for Copyright infringement.
- Operational Insufficiencies
Open-source projects can be a lot of effort for an organization. It isn’t always clear who will do the work to manage the change requests from the developer community or take care of scope, licensing, and versioning.
- Poor Developer Practices
If hackers are invited to contribute to open-source projects, they can potentially change the code so that it contains malware. If the code is not carefully reviewed, it can become part of an open-source project.
Conclusion
Keycloack simplifies a lot of the work that is needed for having an IAM up and running. If your application doesn’t need to make use of a custom authentication system, then using Keycloack would allow you to manage access management scenarios without having to implement everything from scratch. Less development costs, less bugs, more focus on better features. That’s why we would recommend using Keycloack.

